I will share a solution for LootStash challenge of the CTF tryout. I tried two approaches. Simple one and the simpler one. I will start with the simple one. simple solution First of all, download the file and check the file type. It is an ELF file. Let’s execute it and see the result. I … Read More “CTF tryout – LootStash write-up” »
Category: CTF
Description The web project was rushed and no security assessment was done. Can you read the /etc/passwd file? Solution This challenge is about XML external entity Injection. I referred to the document on OWASP. The website looks like below. I noticed the special info changes when I clicked the Details button. I captured the request … Read More “picoCTF – SOAP write-up” »
Description Find the flag being held on this server to get ahead of the competition http://mercury.picoctf.net:45028/ Solution Go to the given link and check the website. There are two buttons. The background color changes as we choose the buttons. I used the Burpsuite to see what was happening behind the scenes. I captured the request moment … Read More “Pico CTF – Get aHEAD write-up” »
Description Can you figure out how this program works to get the flag? Connect to the program with netcat: The program’s source code can be downloaded here. The binary can be downloaded here. Solution We can learn another function of gdb from this challenge. In the question, we are asked to input the address of … Read More “picoCTF – Picker IV write-up” »
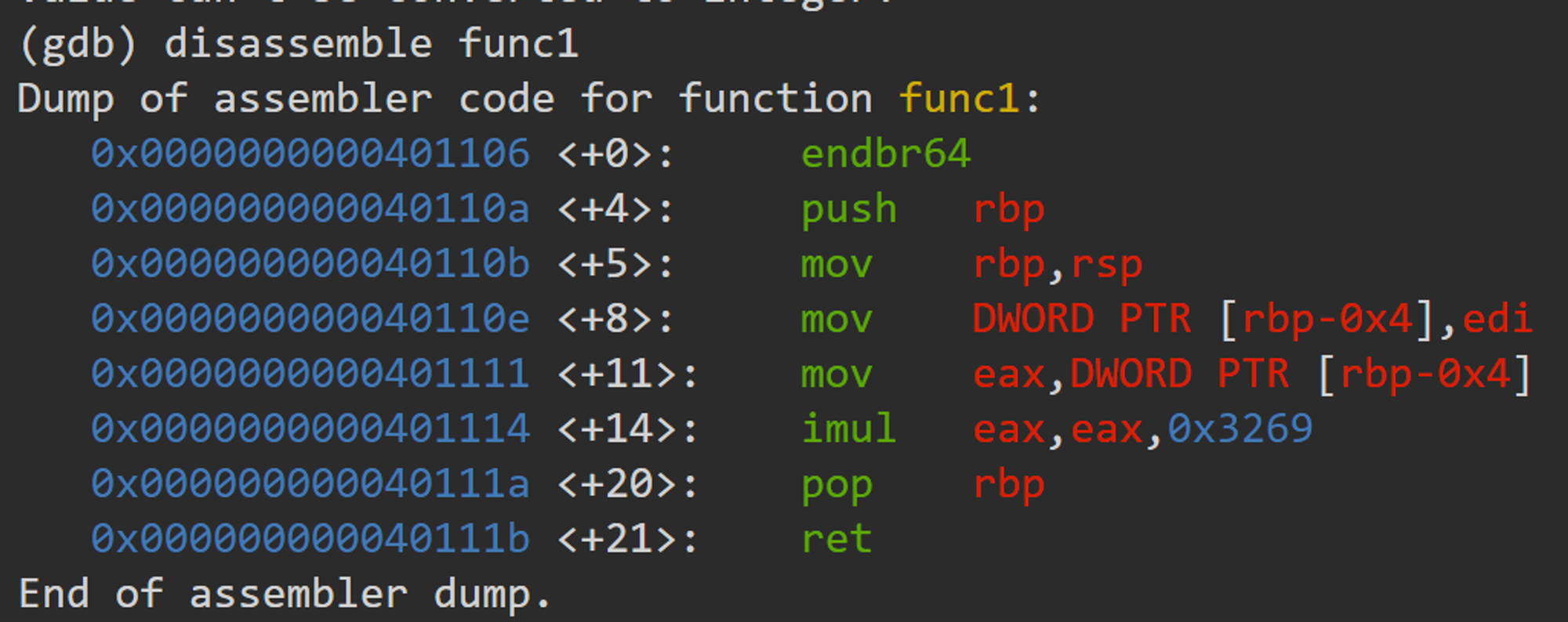
Description main calls a function that multiplies eax by a constant. The flag for this challenge is that constant in decimal base. If the constant you find is 0x1000, the flag will be picoCTF{4096}.Debug this. I think this exercies is very useful. I will share 2 solutions of the exercise. Solution 1 We can simply disassemble the function. If we … Read More “picoCTF – GDB baby step4 writeup” »
Description Reception of Special has been cool to say the least. That’s why we made an exclusive version of Special, called Secure Comprehensive Interface for Affecting Linux Empirically Rad, or just ‘Specialer’. With Specialer, we really tried to remove the distractions from using a shell. Yes, we took out spell checker because of everybody’s complaining. … Read More “Pico CTF 2023 – Specialer writeup” »