Description Find the flag being held on this server to get ahead of the competition http://mercury.picoctf.net:45028/ Solution Go to the given link and check the website. There are two buttons. The background color changes as we choose the buttons. I used the Burpsuite to see what was happening behind the scenes. I captured the request moment … Read More “Pico CTF – Get aHEAD write-up” »
Enumeration nmap Nmap result is as below. Check FTP and SSH ports are open. Also, FTP allows anonymous login. Therefore, login as anonymous. Download all the files and enumerate the directories and files. We can see the users in passwd. netadmin. checked. In the config directory, we can find wireless information. There is the password! … Read More “Hack the box – Wifinetic – writeup” »
Description Can you figure out how this program works to get the flag? Connect to the program with netcat: The program’s source code can be downloaded here. The binary can be downloaded here. Solution We can learn another function of gdb from this challenge. In the question, we are asked to input the address of … Read More “picoCTF – Picker IV write-up” »
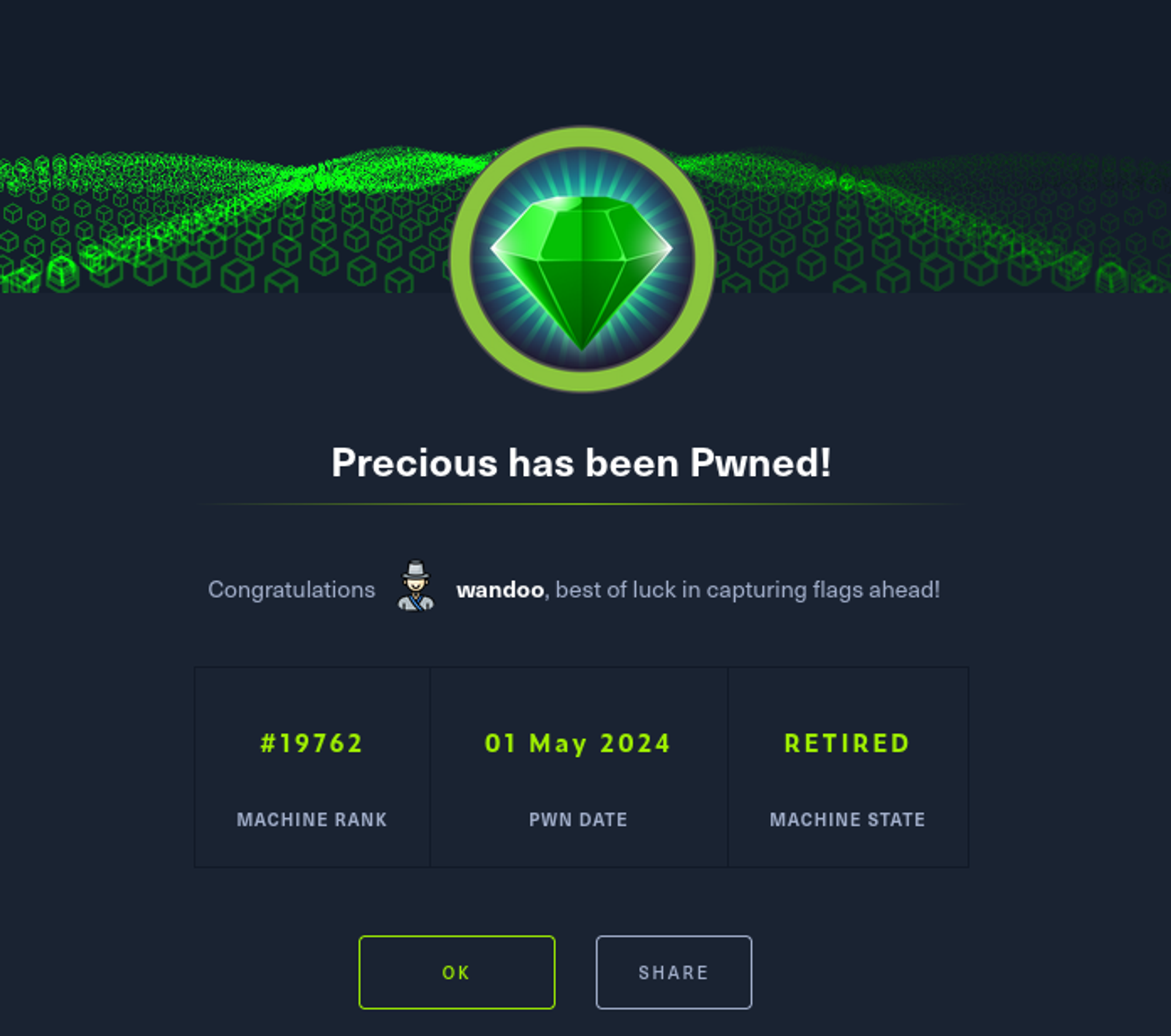
Enumeration Start with an Nmap scan. SSH port and web server are open. However, It failed to redirect to the domain address. Let’s add it to the file. Now, let’s visit the web page and see how it looks. It’s a file conversion web page. I did the Nmap scan again since we added the … Read More “Hack the box – Precious write-up” »
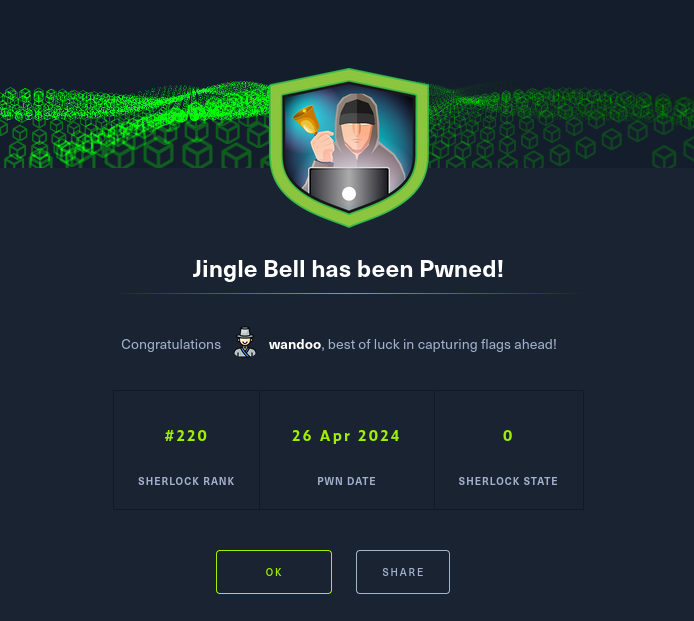
I will walk through Jingle Bell Sherlock. We have a database file. So let’s open it with Sqlite3. sqlite3 wpndatabase.db And let’s see the contents of the database. Ok, I see there is the column called Payload. Which software/application did Torrin use to leak Forela’s secrets? Then you can see Slack is used for communication. … Read More “Hack The Box – Sherlock – Jingle Bell” »
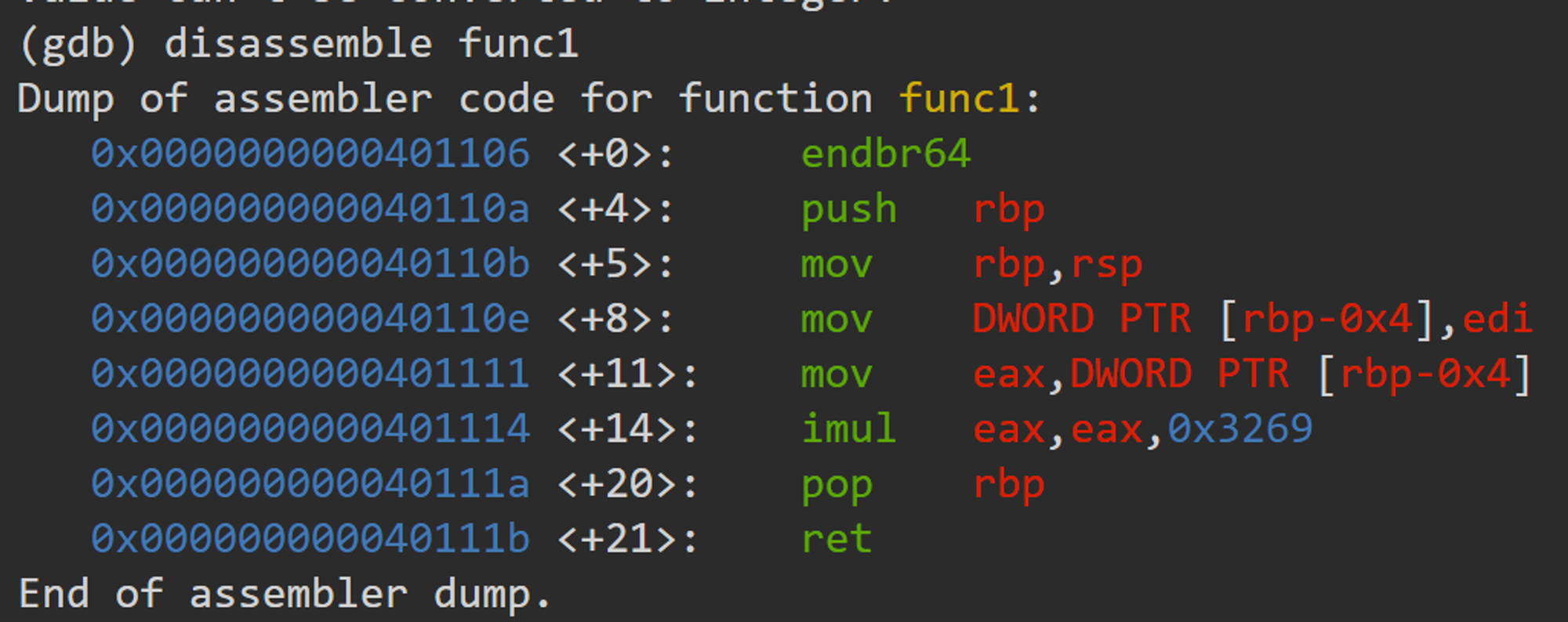
Description main calls a function that multiplies eax by a constant. The flag for this challenge is that constant in decimal base. If the constant you find is 0x1000, the flag will be picoCTF{4096}.Debug this. I think this exercies is very useful. I will share 2 solutions of the exercise. Solution 1 We can simply disassemble the function. If we … Read More “picoCTF – GDB baby step4 writeup” »