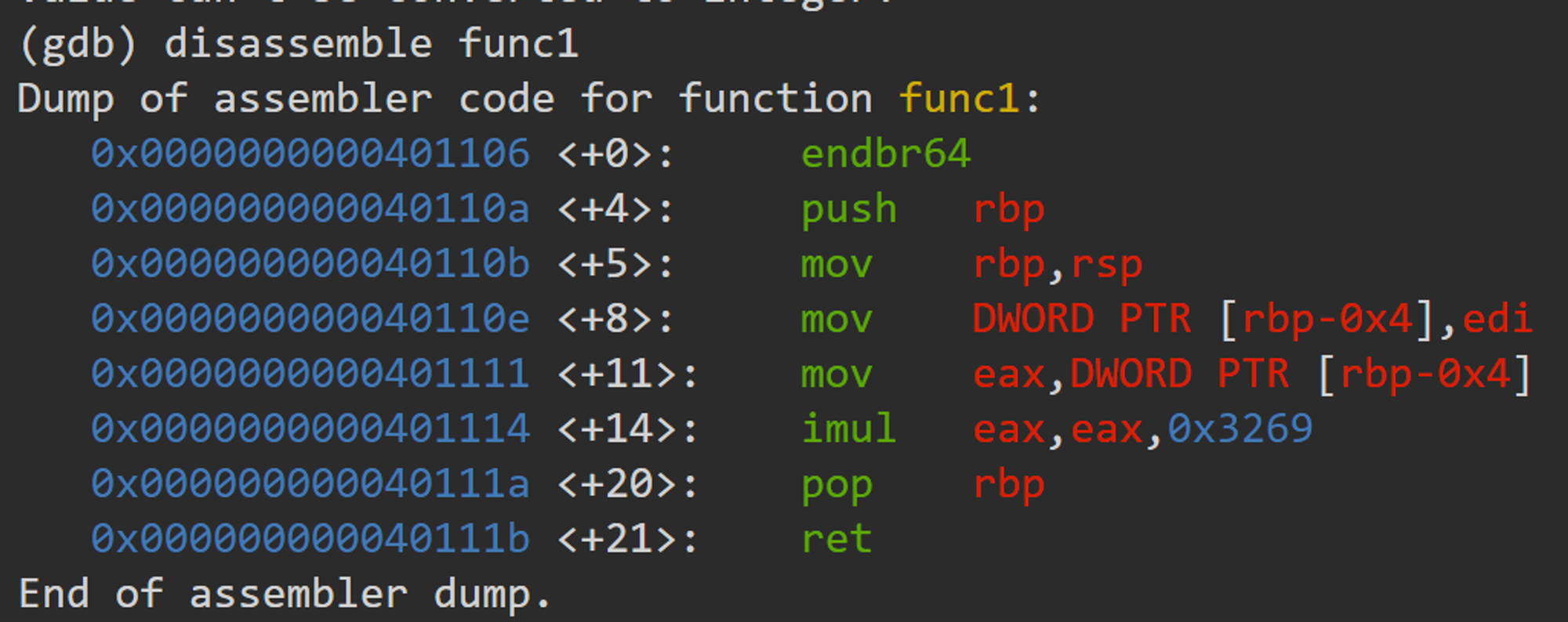
Description main calls a function that multiplies eax by a constant. The flag for this challenge is that constant in decimal base. If the constant you find is 0x1000, the flag will be picoCTF{4096}.Debug this. I think this exercies is very useful. I will share 2 solutions of the exercise. Solution 1 We can simply disassemble the function. If we … Read More “picoCTF – GDB baby step4 writeup” »
Description Reception of Special has been cool to say the least. That’s why we made an exclusive version of Special, called Secure Comprehensive Interface for Affecting Linux Empirically Rad, or just ‘Specialer’. With Specialer, we really tried to remove the distractions from using a shell. Yes, we took out spell checker because of everybody’s complaining. … Read More “Pico CTF 2023 – Specialer writeup” »
To solve this challenge, we need an understanding of references in headers. We will use this reference throughout the challenge. Q1. Only people who use the official PicoBrowser are allowed on this site! Change the user-agent to PicoBrowser. Q2. I don’t trust users visiting from another site. The Referer header allows a server to identify referring pages … Read More “picoCTF2021 – who are you? writeup” »
Enumeration The nmap result tells us the FTP server and web server are open. The version of the web server is IIS 7.5. For the FTP server, it allows anonymous login. Also, we know that there are iisstart.htm and welcome.png files. If we visit the website, we can check these two files. Using the FTP … Read More “Hack the box – Devel writeup” »
Enumeration Scan the target machine with nmap. The web server and ssh are open. Let’s check the web server first. If we go to the page, we see the image file saying Don’t Bug me! I couldn’t find any useful information on the web page and the source code. There must be something we can … Read More “Hack the box – Shocker (CVE-2014-6271)” »
Enumeration Got the following result from the Nmap scan. I can see web servers are open and the nmap script’s saying changelog.txt is interesting. If we visit the web page, we can see the login page. I tried logging in with the default credentials for pfsense. admin:pfsense However, I failed. Let’s check the changelog.txt file … Read More “Hack the box – machine – Sense” »