Exercise 1 Analyze the execution header. Check the first 15 lines of binaries from the file using xxd. In the first line, it can be seen that the magic byte of the ELF header starts with 0x7f. To understand what the following bytes mean, I used readelf command. The descriptions of each byte in the … Read More “Practical Binary Analysis chapter2 exercises” »
Tag: binary
This post is the second part of the post. strace, ltrace Let’s run the file again but this time providing a random string. Now a new reply appears on the screen. Let’s try with the string discovered. It still ends up with the error but it returns ok. We are getting there! It is able … Read More “Chapter 5 of Practical Binary Analysis Review 2” »
This post will explain the exercise from chapter 5 in the textbook “Practical Binary Analysis Build Your Own Linux Tools for Binary Instrumentation, analysis, and Disassembly (Andriesse, Dennis) “ The post will be divided into 2 parts. Many tools will be mentioned in this post. The textbook asks us to find a flag in the … Read More “Chapter 5 of Practical Binary Analysis Review 1” »
Description Can you figure out how this program works to get the flag? Connect to the program with netcat: The program’s source code can be downloaded here. The binary can be downloaded here. Solution We can learn another function of gdb from this challenge. In the question, we are asked to input the address of … Read More “picoCTF – Picker IV write-up” »
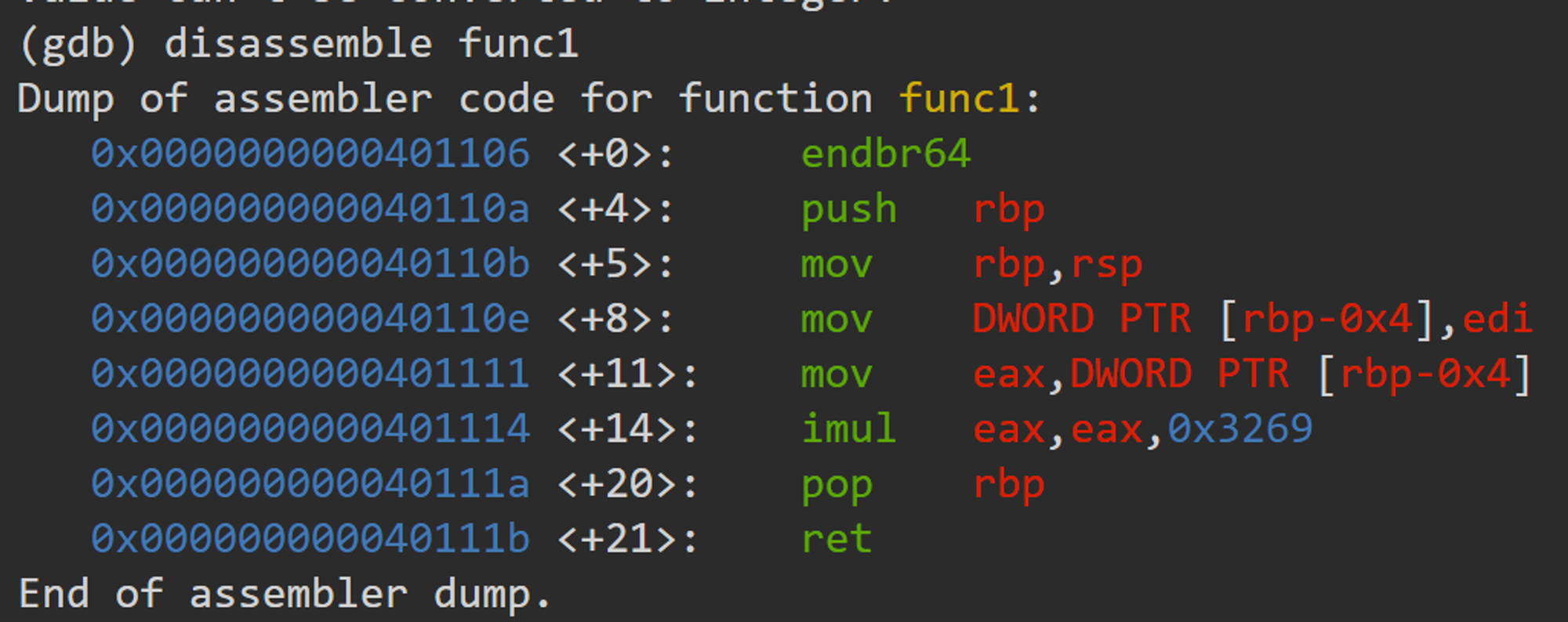
Description main calls a function that multiplies eax by a constant. The flag for this challenge is that constant in decimal base. If the constant you find is 0x1000, the flag will be picoCTF{4096}.Debug this. I think this exercies is very useful. I will share 2 solutions of the exercise. Solution 1 We can simply disassemble the function. If we … Read More “picoCTF – GDB baby step4 writeup” »